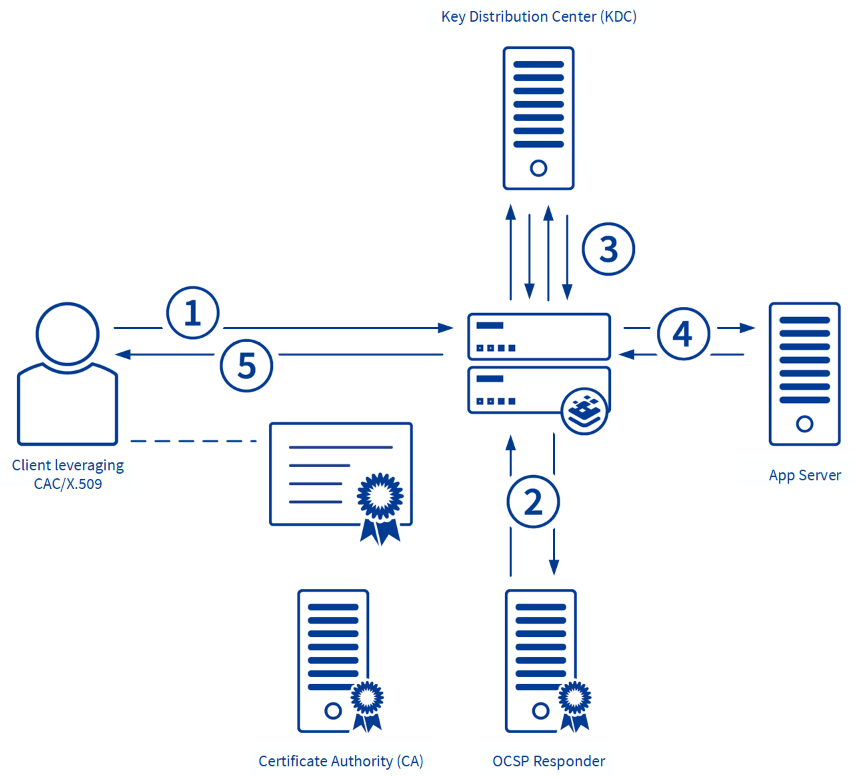
Dod Safe Cac Login
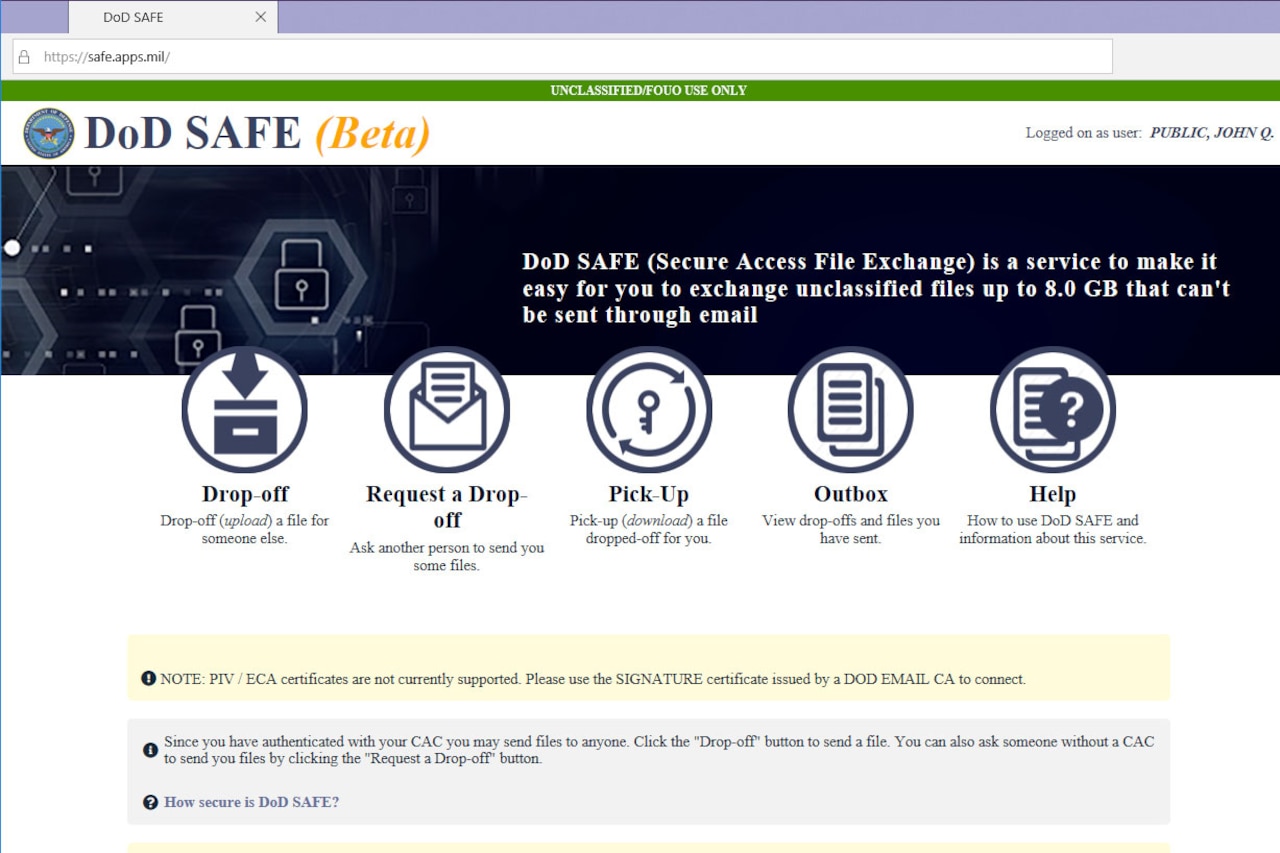
Dod Safe Cac Login - All accesses to data on dod safe are logged and can be easily checked if you are ever concerned that a 3rd party might have gained access to your data. Users are advised to read and agree to the security notice. Users are advised to read and agree to the security notice. This department of defense internet computer system is subject to monitoring at all times. Furthermore, uploaded data is only held on dod safe for a maximum of 7 days, after which time it is automatically deleted. Users are advised to read and agree to the security notice. Users are advised to read and agree to the security notice. This department of defense internet computer system is subject to monitoring at all times. This department of defense internet computer system is subject to monitoring at all times. This department of defense internet computer system is subject to monitoring at all times. This department of defense internet computer system is subject to monitoring at all times. Users are advised to read and agree to the security notice. Users are advised to read and agree to the security notice. Users are advised to read and agree to the security notice. This department of defense internet computer system is subject to monitoring at all times. This department of defense internet computer system is subject to monitoring at all times. This department of defense internet computer system is subject to monitoring at all times. All accesses to data on dod safe are logged and can be easily checked if you are ever concerned that a 3rd party might have gained access to your data. Furthermore, uploaded data is only held on dod safe for a maximum of 7 days, after which time it is automatically deleted. Users are advised to read and agree to the security notice. This department of defense internet computer system is subject to monitoring at all times. This department of defense internet computer system is subject to monitoring at all times. Users are advised to read and agree to the security notice. Users are advised to read and agree to the security notice. This department of defense internet computer system is subject to. Users are advised to read and agree to the security notice. Users are advised to read and agree to the security notice. Users are advised to read and agree to the security notice. Users are advised to read and agree to the security notice. Furthermore, uploaded data is only held on dod safe for a maximum of 7 days, after. This department of defense internet computer system is subject to monitoring at all times. Users are advised to read and agree to the security notice. This department of defense internet computer system is subject to monitoring at all times. Users are advised to read and agree to the security notice. This department of defense internet computer system is subject to. Users are advised to read and agree to the security notice. Users are advised to read and agree to the security notice. This department of defense internet computer system is subject to monitoring at all times. Users are advised to read and agree to the security notice. All accesses to data on dod safe are logged and can be easily. This department of defense internet computer system is subject to monitoring at all times. Users are advised to read and agree to the security notice. This department of defense internet computer system is subject to monitoring at all times. Users are advised to read and agree to the security notice. Users are advised to read and agree to the security. This department of defense internet computer system is subject to monitoring at all times. Users are advised to read and agree to the security notice. All accesses to data on dod safe are logged and can be easily checked if you are ever concerned that a 3rd party might have gained access to your data. This department of defense internet. Users are advised to read and agree to the security notice. This department of defense internet computer system is subject to monitoring at all times. Users are advised to read and agree to the security notice. This department of defense internet computer system is subject to monitoring at all times. All accesses to data on dod safe are logged and. All accesses to data on dod safe are logged and can be easily checked if you are ever concerned that a 3rd party might have gained access to your data. Furthermore, uploaded data is only held on dod safe for a maximum of 7 days, after which time it is automatically deleted. Users are advised to read and agree to. Furthermore, uploaded data is only held on dod safe for a maximum of 7 days, after which time it is automatically deleted. This department of defense internet computer system is subject to monitoring at all times. This department of defense internet computer system is subject to monitoring at all times. All accesses to data on dod safe are logged and. Users are advised to read and agree to the security notice. This department of defense internet computer system is subject to monitoring at all times. Furthermore, uploaded data is only held on dod safe for a maximum of 7 days, after which time it is automatically deleted. This department of defense internet computer system is subject to monitoring at all. This department of defense internet computer system is subject to monitoring at all times. Users are advised to read and agree to the security notice. This department of defense internet computer system is subject to monitoring at all times. Users are advised to read and agree to the security notice. Furthermore, uploaded data is only held on dod safe for a maximum of 7 days, after which time it is automatically deleted. All accesses to data on dod safe are logged and can be easily checked if you are ever concerned that a 3rd party might have gained access to your data. This department of defense internet computer system is subject to monitoring at all times. Users are advised to read and agree to the security notice.DoD CAC Authentication Kemp Support
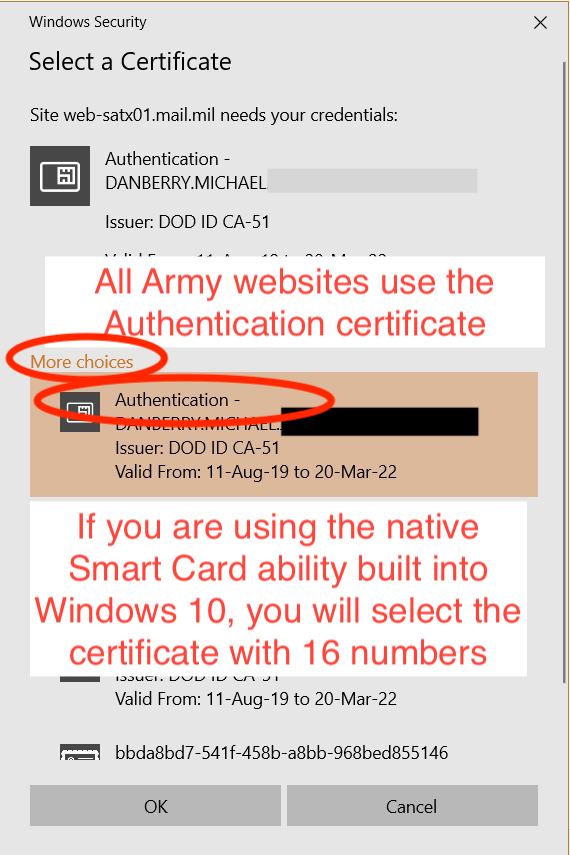
MilitaryCAC's Use your CAC on Windows 10
DOD Agency Keeps File Swaps Safe > U.S. Department of Defense > Story
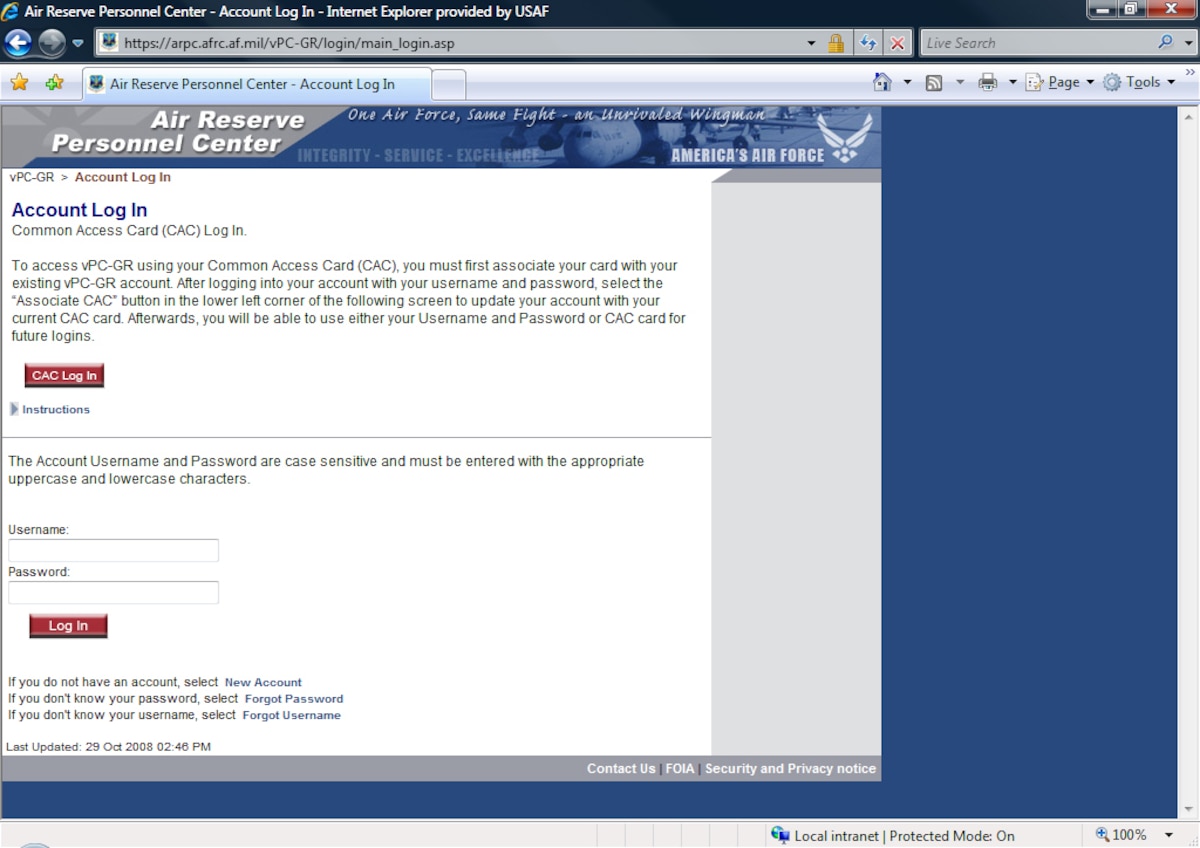
CAC login makes access easier for reservists > Air Force Reserve Command > News Article
Keep your common access card safe, secure > Hill Air Force Base > Article Display
Defence Common Access Card (CAC) Checkpoint Visitor Management EvTrack Visitor Management
How To Digitally Sign A Pdf With Cac On Mac Answer Key Pdf
Enabling Web Apps For DoD Security via PKI/CAC Enablement
DoD SAFE Login
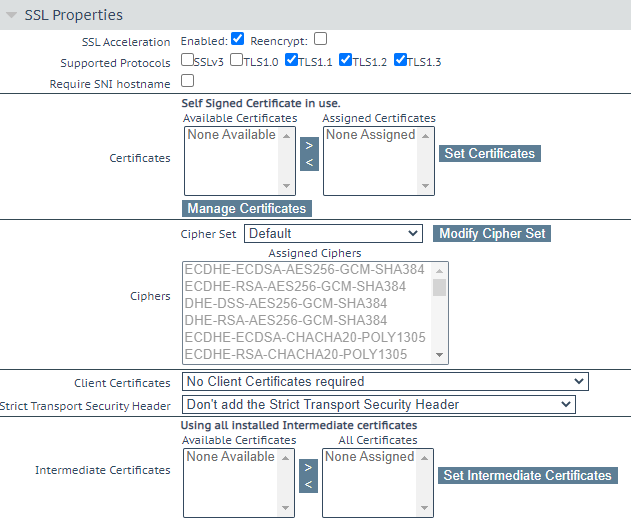
DoD CAC Authentication Kemp Support
This Department Of Defense Internet Computer System Is Subject To Monitoring At All Times.
Users Are Advised To Read And Agree To The Security Notice.
Related Post: